Although the internet has upgraded our lives today, it has also presented a challenge to data security. While most of us, especially preppers, may prepare for common threats by taking preventative measures and knowing basic survival skills, only some are constantly on guard for the possibility of cybercrime. Preppers must act proactively to protect their money from online risks to prevent being a victim of cyber attacks.
You can protect your money from cyber attacks by using strong passwords, enabling two-factor authentication, and updating your device regularly. You can also avoid clicking on dubious links, use an antivirus program, exercise caution when using public Wi-Fi networks, and consider using a VPN.
Outwit these online hackers by following tips on protecting your money from cyber attacks. Continue reading to learn more.
Quick Navigation
- Common Types of Cyber Attacks on Money
- How to Protect Your Money from Cyber Attacks
- What to Do If Your Money is Stolen
- Conclusion
Common Types of Cyber Attacks on Money

A cyber attack means a third party, a hacker, has unauthorized access to a system, account, or network.
Cyberattacks have several detrimental repercussions. They may result in data breaches, which may cause data loss or manipulation and money loss.
Companies that fall victim to such attacks may suffer financial losses, decreased consumer trust, and reputational harm. Your reputation and safety risk may also result from these assaults.
Phishing Attack
Phishing is a kind of internet attack in which cyber criminals pose as a reliable contact and send the victim phony emails.
Unaware of this, the owner or victim opens the phishing email and either downloads the attachment or opens the malicious link. Cyber thieves can obtain private data and login passwords this way.
Malware Attack
Malware are harmful software viruses such as worms, spyware, ransomware, adware, and trojans.

The trojan infection poses as trustworthy software. Spyware is software that secretly takes all your private information, while ransomware shuts down access to the network’s essential parts.
Malware enters a network by exploiting a weakness. These weaknesses happen when someone visits a risky link, downloads an email attachment, or uses an infected pen drive.
Ransomware
A ransomware attack intends to prevent access to a computer system or data until a paid ransom. Phishing emails, malicious advertising, accessing infected websites, and vulnerability-based attacks are all ways ransomware spreads.
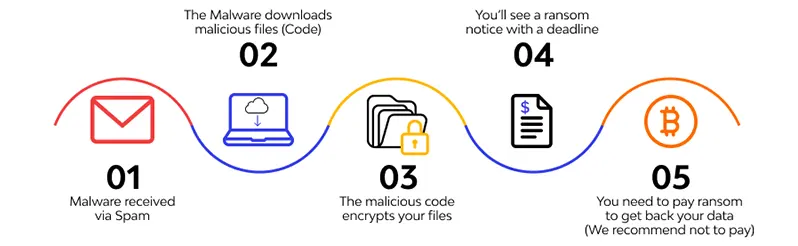
Data breaches, leaks, intellectual property theft, and downtime are all consequences of ransomware attacks. Ransomware may encrypt all or specific data after installation.
A ransom message that follows the first ransomware infestation explains why the files are unavailable.
A ransom payment may cost a few hundred to several hundred thousand dollars (or even Bitcoin).
Others
Other types of cyber attacks include:
- Identity theft
- Spamming
- Spyware
- Adware and more
How to Protect Your Money from Cyber Attacks
Here are some helpful solutions to help you safeguard your money and financial data online:
Create Strong Passwords
Remember that a longer password is more secure. A strong password has at least 12 characters and is hard to crack.

The best technique to make a lengthy password you will remember is to use a sentence and then change some special characters and add numbers. You can also use a unique password generated by a password manager.
If you currently use these sample passwords — 11111, 123456, or any other sequential number — change them as soon as possible since they are among the most popular and straightforward to break.
Turn On Two-Factor Authentication
Two Factor Authentication. Multifactor authentication. Two-step verification. MFA. 2FA. All of these refer to taking an additional security step when websites and apps ask you to verify your identity.

This authentication wants to make sure you are the one accessing your information anywhere and anytime.
You will start to see requests for multifactor authentication everywhere. Your email account should come first, followed by your bank accounts, social media accounts, and online shops, and remember your gaming and streaming entertainment options!
Keep Your Software Up-to-Date
Always check whether your computer’s operating system and installed software have the most recent upgrades. By doing this, operating system and application vulnerabilities used by malicious software and assaults would lessen.
Whether you are using the most recent OS, XP, or Windows 7, security is crucial since Windows OS devices are often targets of vulnerabilities. Take advantage of automatic upgrades for all your operating systems.
Install Antivirus
You can use application and software-based firewalls and a basic firewall for increased protection.

With a comprehensive anti-malware solution, you can stay safe against Trojan viruses, worms, and other threats. Some anti-malware products have unique technologies that add extra security when using online banking and shopping websites.
Be Wary of Suspicious Emails and Links
Most financial institutions will only contact consumers if they ask them to provide personal information or input personal information.
Instead of clicking on a link, manually input the URL whenever you need to access an online bank, merchant, or payment website. Visit web pages without clicking on:
- Emails with links
- Social networking site messages
- Chat room messages
- Advertising banners that appear on dubious websites
- Links that strangers have sent to you
Monitor Your Accounts Regularly
Your bank or checking accounts are not static if you routinely pay and make purchases. Monitoring your account may be beneficial since the money comes in and goes out.
Regularly monitoring your account will help you identify possibly fraudulent activity and stop financial losses in their tracks.
An identity thief could, for instance, get your debit card information and use it to make a minor test purchase in the hopes that you won’t notice. The thief could use your account to make other, more significant transactions if the transaction goes through.
Use a VPN
You can establish a safe connection between your computer and the internet through a tool called Virtual Private Network (VPN). All your web traffic while using a VPN is encrypted and sent via a server in your chosen area.

You can protect your sensitive information using a VPN. This security is helpful, especially for your passwords, credit card numbers, bank account information, and personal documents.
A VPN may protect your data from snoopers even if you utilize public Wi-Fi networks, which are often unsecured and open to assaults.
It can defend you against phishing and malware assaults that deceive you into opening dangerous files or clicking on the wrong links.
Avoid Public Wi-Fi for Financial Transactions
Avoid utilizing public computers in airports, bars, cafes, hotels, public libraries, or other places when logging in to online banking services or online retailers.
These public computers can be running several spyware applications. If true, these malicious apps might intercept internet traffic and record everything you input on the keyboard, including your passwords.
The traffic on a public Wi-Fi network may be intercepted by the network’s administrator or cybercriminals, opening the door for attacks via network worms.
Backup Your Important Data
You must have your sensitive data backed up in the case of a catastrophe (typically a cyberattack) to prevent significant downtime, data loss, and financial loss.
Make electronic copies of your key documents, data, and finances, and store them securely.
As appropriate for the sensitivity of the data, have several backup strategies to completely secure your work (such as cloud storage, an encrypted flash drive, or an external hard drive).
Secure Your Device
You will lose your personal information, money, and valuable data if your mobile device is lost, misplaced, or stolen. Protect your equipment by:
- Installing a virus protection software
- Setting an unlocking password, gesture, or fingerprint
- Creating a password requirement before app installation
- Turning off automatic network connection and hiding Bluetooth while not in use
- If your device enables it, allow remote locking or wiping features.
What to Do If Your Money is Stolen

If you lose money or have been a cyberattack victim, follow these steps accordingly.
1. Contact the financial institutions where you have accounts, including banks, credit card firms, and other businesses. It’s crucial that cyber-attacked accounts need to be on hold. Any unlawful credit or charge accounts should be closed. Inform the authorities if you suspect identity theft.
2. Inform the FBI Internet Crime Complaint Center (IC3) of your complaint. After reviewing the complaint, they will forward it to the proper authority.
3. If your card has a fraudulent transaction, report the scam immediately to your card issuers. You might also get in touch with your bank to hold accounts.
4. Report the event to the police for proper documentation.
5. Most importantly, change your logins and passwords as soon as possible.
Conclusion
In the current digital era, safeguarding your money from cyberattacks has become crucial to managing your finances.
Preppers may lessen the dangers of cyber assaults and better safeguard their money using the advice and techniques provided in this article.
Remember that your financial security should always come first in the digital sphere, along with being educated and vigilant.
Take proactive measures to protect your money from online hazards now more than ever, with the incidence of cyber attacks on the rise.
